Here is how you set a static IP for a OpenVPN client setup through your pfSense router. We needed this for printing from one network to the other, when using the OpenVPN software client.
It might depend on how you setup your OpenVPN in the beginning, but this is what worked for me.
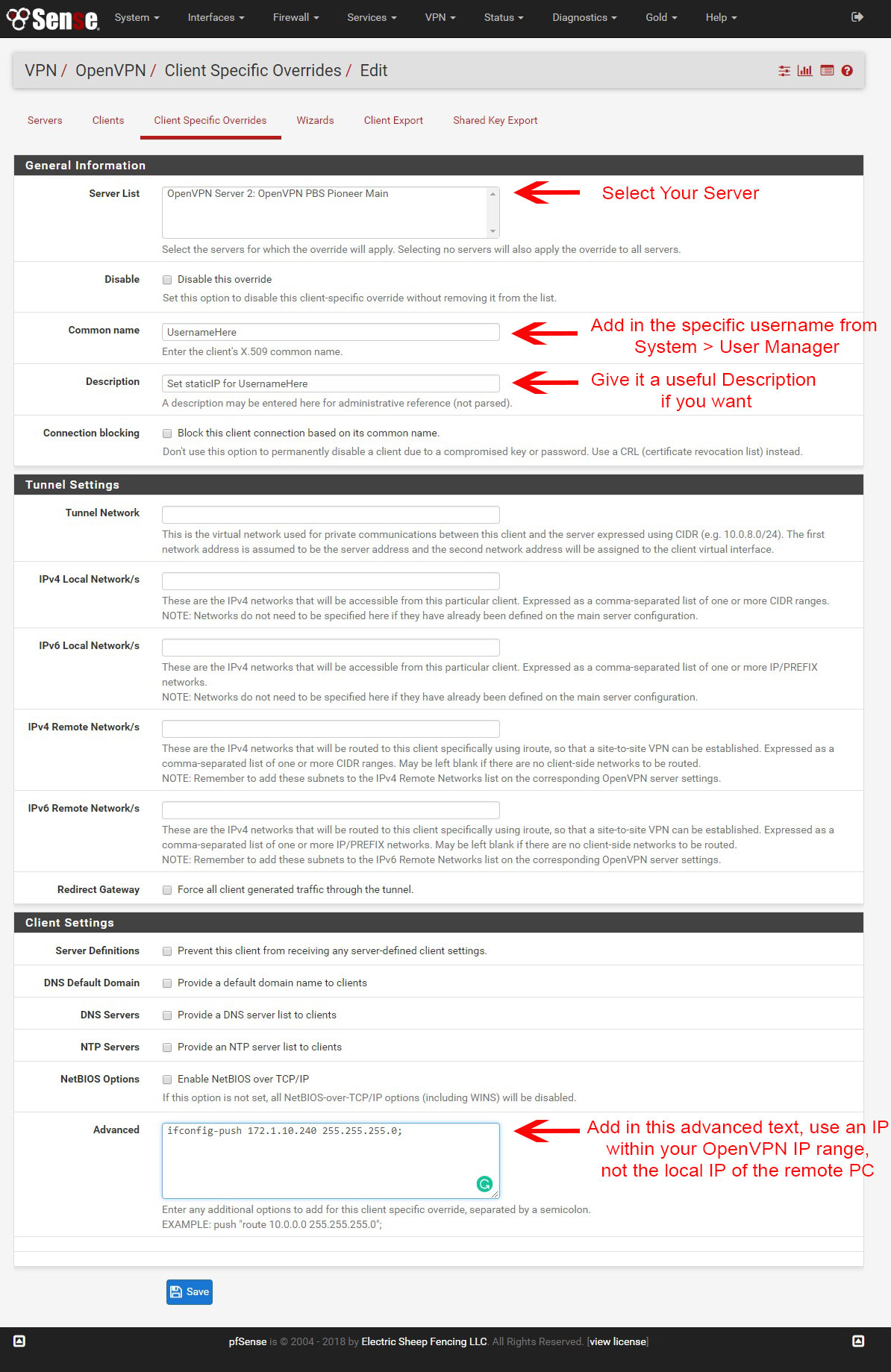
We have each client setup with their own username and password under System > User Manager
How to set the static IP is you go to VPN > OpenVPN > Client Specific Overrides
Click the green plus
You only need to do a few things to get this to work.
Server List Select your server from the list, I only had one.
Common Name Enter the Username of the person that you created in the User Manager.
Advanced ifconfig-push 172.1.10.240 255.255.255.0;
Type that info into the Advanced field, make sure you use an IP address within the range of the OpenVPN. Not the local IP for the PC. (It should have a local IP and the OpenVPN IP.
Click Save
You will need to disconnect and reconnect the OpenVPN client if its already connected
See picture below


Hey,
thanks for the helpful explanation. This really works just as you would expect!
Only one thing to work around here: OpenVPN does not recognize the IP you set this way as already assigned. So, if you assign e.g. 172.1.10.15 to one client – this works fine first. But as soon as the 16th client connects, OpenVPN will try to assign the .15 to this client, too.
So make sure, the static assignment in the override is outside of the range that is available for “regular” clients.
In my case, I have set “concurrent connections” to 25 (in OpenVPN -> Servers -> Config), so there is a good chance that IPs higher than .26 will never get automatically assigned to clients. My “statics” are therefore from .50 upwards to allow for some extra space, just in case…
Thanks for noticing that, its why I added .240 into the range, but didn’t mention it for other people to know about, good catch.
Hi i have a problem with this approach! Traffic doesn’t flow for those clients with IP reservation falling out of the tunnel range of the server configuration. I need to reserve and be sure no one else is going to use such ip with wrong auth or certificate. Any idea why and how to fix it? Thanks
So your having a problem with clients set with a static IP outside of the DHCP range on the router(local network)?
OR Outside of the DHCP range of the OpenVPN DCHP?
If its the latter I really don’t know, I haven’t ever tried that, i just made sure it was a really high one so no one else on our network would try grab it.
IMHO the Common Name must match the user’s common name in their certificate, NOT the regular username.
Depending upon your local requirements, the username and common name might be the same, however thats not certain.
YMMV
Not sure, this is how we do it and it works!
“No Name” is talking about imported certs for users. Cause they might have different CN than usernames. In case of generating them automatically (most common approach) CN value is taken from the username – so no issue. Seems like he had to work with imported ones 😉
Just tested it and works for me to. Yes I thought it would need to match the common name of the certificate too but it doesn’t. The client name works.
Thank you very much. Worked like a charm.
Thank you very much!
I can confirm that the common name is actually the “username” and NOT the certificate name for the user, the PFsense documentation is wrong in this case. That’s what I was struggling with for a while until I found this write-up and it works perfectly.
Thanks again!
Arman
HI,
Clients getting the static IP but after a while the ip while change to a other static IP. Any idea what setting i’ve missed?
Never mind….. Did a typo at IP 😉
HI,
My openVpn server have LDAP configure with autentification, Is there any way to have a static ip on the clients?
Thanks